21 September 2013:
“RSA Warns Customers Off Suspected NSA-Tainted Crypto Tools” 
In the article linked to above, Seidenberg professor Darren Hayes speaks to the ECT News Network about complications between technologies and security protocols. The topic has been heavily circulated in the media and through academia since humanity’s pronounced dependance on technology and even more so since the recent events concerning the NSA, national security, and privacy of US Citizens. The specific technology discussed in the article is the Dual Elliptic Curve Deterministic Random Bit Generator (Dual_EC_DRBG).
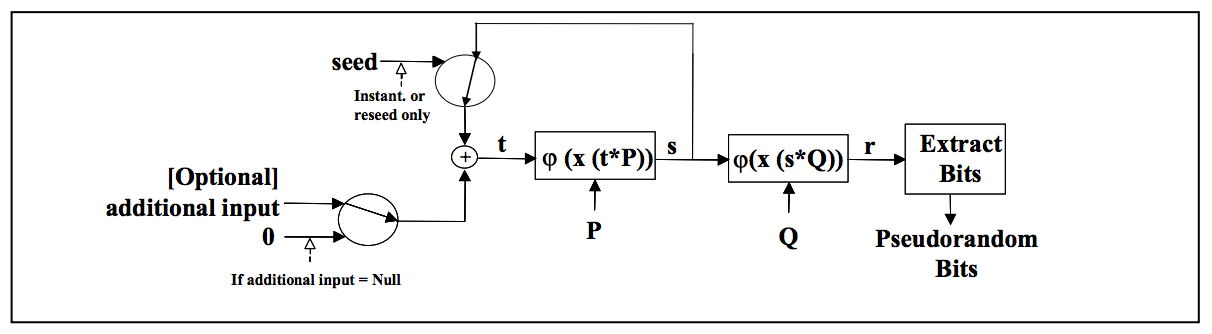
“The Dual_EC_DRBG is a PRNG [pseudorandom number generator] based on the elliptic curve discrete logarithm problem, the idea being that finding the discrete logarithm of a random elliptic curve element with respect to a publicly known base point is not feasible. The bigger the elliptic curve, the more difficult it is to find that discrete log.
The problem is that there is a backdoor in the NIST SP800-90 Dual-EC-PRNG standard. This was first discovered by Microsoft researchers Dan Shumow and Niels Ferguson, who discussed their findings at a Crypto 2007 rump session.”
Hayes works alongside many projects in technological cryptology and security and these issues often present themselves as fruitful topics of debate across the globe.