No phone’s secret is safe from the forensic skills of Seidenberg’s James Ossipov and Dr. Darren Hayes. At first glance, it appears that James is ironing a piece of paper, but what is under the paper is what is helping law enforcement retrieve photos, texts, and various information from most phones—even if it’s deleted.
Dr. Darren Hayes, professor at Seidenberg, and James Ossipov have been working together with a method of evidence extraction called JTAG, which in time could revolutionize the way law enforcement agencies use computer forensics.

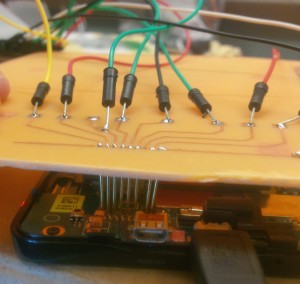
Hayes mentions that, “James is actually working on a project where we are trying to automate something called JTAG. JTAG is accessing user data on a phone when you can’t use traditional methods for extracting evidence from a phone. So, we extract evidence directly from the printed circuit board using JTAG. Sometimes a phone may have encryption, so you need JTAG for that. Sometimes the phone is damaged, for instance, someone may have dropped it in water, and therefore JTAG is your only method to get the phone’s data. JTAG is the only option for examining Windows smartphones.”
JTAG sounds like an amazing innovation to restore information from a phone, even if it is damaged. However, this method is not for everyday use yet — it is primarily used in investigations to retrieve evidence.
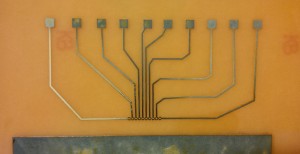
“This method is generally only used by law enforcement. Many law enforcement agencies don’t have the capabilities to perform JTAG, so they have to bring in outside experts. What we are trying to do is make it easier for law enforcement by automating the process so more law enforcement agencies can actually use this method of extracting evidence.”
Unfortunately for law enforcement, this method of extracting data cannot be used on an iPhone.
“iPhones are very tricky. They have very good security and are well locked down,” says Hayes. “You can’t perform chip off, meaning you cannot take a memory chip from an iPhone and put it into another phone because all of the firmware, the system software, is mapped to the memory chip. So, if you try to move it to another phone, you won’t be able to access it. But LG phones and Samsung’s are the easiest phones for this process.”
Computer forensics is advancing every day and Seidenberg is proud to be at the forefront of it all. If you are interested in learning about computer forensic, Dr. Darren Hayes is currently teaching a Cyber Law Class (CIT 363). If you’re not registered for that class, don’t worry—in the fall he is offering a Mobile Forensics course where he will teach how to extract evidence from mobile devices and obtain evidence from third-parties such as Facebook.
Also worth mentioning is that James also worked on JTAG last semester with two other veterans (David Cano – Navy & Gordon Wildrick III – Marines), and he himself is a veteran of the Army. We’re proud to support our forces and we’re more proud of the work they’ve accomplished with Seidenberg.

