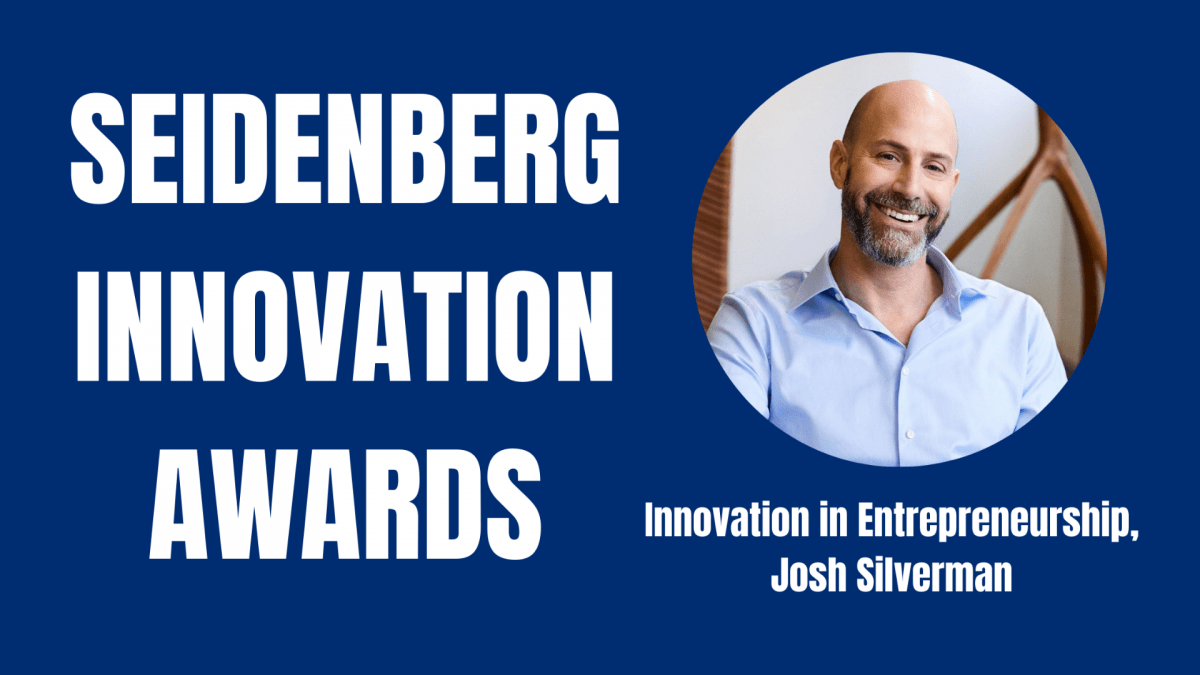
The Spring 2021 session of Pace University’s Seidenberg Innovation Awards has officially wrapped up with yet another notable honoree: Josh Silverman, the CEO of Etsy. During this annual event, Josh Silverman was praised for setting an example for entrepreneurs, while also supporting the business and technology communities within the Seidenberg School of CSIS. With experience in various fields, Josh Silverman eventually settled into his current position with one of the largest e-commerce businesses in America. However, one of the first steps in his career path was not business but instead public policy. After studying public policy at Brown University and working in the field for a few years, Silverman decided to go back to school for business at Stanford. Upon graduating, one of his first jobs in the field was working for a small, lesser-known company. Although his position provided him with more responsibilities than expected, it also led to him gaining invaluable experience and knowledge that would prepare him for his future role at Etsy.
WHAT IS ETSY?
So, what is Etsy? Although many of you may already know, Etsy is an e-commerce company that allows entrepreneurs to sell vintage and/or homemade products online. Through Etsy, selling is made significantly easier so that sellers, creators, and innovators can focus more on the creation and distribution of their products. Because of this, Etsy serves as a sound platform for facilitating the needs of smaller businesses, with some of them being owned by our very own Pace students.
SUPERMOON JEWELRY
First up is SuperMoon Jewelry, which offers statement pieces ranging from rings to necklaces and more. Whether you decide to order a pair of celestial earrings, an astrology-inspired necklace, or a surprise mystery box, just know that you’ll be supporting one of our very own. The owner of this online shop, Theresa Rodriquez, is a Childhood Education major at our New York City campus. On the Etsy webpage for her shop, you’ll see all of her creations, in addition to SuperMoon Jewelry’s Instagram: @shop.supermoon.
JESSICA ANNE RUBIN
Jessica Anne Rubin is an Art major at Pace whose shop features vibrant, uniquely shaped jewelry. With some earrings taking the shape of popular fruits such as strawberries and oranges, her other pieces are equally as fun and eccentric. If you’re looking for accessories that’ll make you stand out, then Jessica Anne Rubin is the perfect place to stop. On her shop’s Instagram, @jessicaannerubin, you’ll also find creative ways to style your new statement pieces.
CHARMED BITCHCRAFT
This shop, created by two friends and recent graduates Julia and Eena, features a variety of products such as spell jars in the form of earrings, necklaces, and more. Depending on what you need, each individual spell jar is filled with the right components for different spells regarding protection, purification, happiness, and self-love. This shop is the perfect place for those who find solace in witchcraft or for those who simply want to support our city witches.
MAKING WISE BUSINESS DECISIONS
When it comes to leading Etsy, one of the most important things to consider as its CEO is ensuring the company’s success. For Silverman, this is determined by the overall success of the platform’s sellers. Essentially, when the sellers succeed then so does the company. Aside from this, there are other components responsible for Etsy’s upward progression. For instance, working with companies that provide useful business tools is an easy way to improve the user experience without the pressure of having to create the tools themselves. An example of one such company would be Braze, whose products specialize in deepening the relationship between businesses and their consumers. One product of theirs that Silverman points out as particularly helpful is their tool called Segment – adept at customizing the user experience based on customers’ wants and needs. With instruments like this in place, more attention can be spent on the other operations needed to sustain Etsy.
The choice to utilize Segment is a perfect example of effectively discerning the best possible business decision. According to Silverman, most advances should take into account two things: time efficiency and optimal economic outcomes. Although the most ideal advancement would include both, it is not uncommon for improvements to be made based on only one out of the two. In this case, using Segment covered both bases. Implementing tools like Segment that maximize company efficiency was especially important for maintaining a steady workflow during the start of the pandemic.
A SHIFT IN E-COMMERCE
One result of the pandemic, particularly during quarantine, was that the portion of Americans who typically opted out of online shopping now needed to. With things that were once easily accessible being difficult to obtain, such as cleaning supplies and toilet paper to name a few, e-commerce quickly became a reliable source during dark times. However, among the usual items that people normally purchased in-store, there was one thing that customers needed desperately and fast: masks.
In a podcast interview with Marketplace Tech, Silverman recounts that after observing this pressing need, Etsy put out a call for sellers with the right materials to start producing masks. This call came about not too long after the start of the COVID-19 pandemic (in March 2020), specifically when the shortage of masks began. With the overall increase of e-commerce alongside the growing need for masks, Etsy’s sales went up as well, thus providing an opportunity for entrepreneurs to support themselves during a time of crisis.
PUTTING THE PIECES TOGETHER
Josh Silverman has not only encouraged entrepreneurship through his support of the Pace community, but he has also encouraged it through the opportunities he has provided through Etsy. As someone who started off in pursuit of one career and ended up in another, Silverman has shown that there’s nothing wrong with taking a different path. In fact, it was each varying step in his journey that prepared him to excel in the exact work he does now.
From one life stage to the next, Silverman has proved that learning doesn’t end with school, but is instead a lifelong, continuous endeavor – especially in business and technology. It is being open to new knowledge that allows entrepreneurs to try different things before settling on the right decision. Needless to say that when doing so, mistakes are all but inevitable. However, it is not the mistakes themselves that are concerning, but rather the kind of lessons you learn from them. Silverman’s career journey is the embodiment of trying new things, seeing what works, and adapting. If there’s anything to take away from his experience, it is that applying these principles can be widely useful in both your personal and professional lives. Interested in exploring a new field? If so, try taking a class or securing a related internship. If there’s a new hobby you’ve been dying to try then maybe find a way to get started. Pursuing that goal or taking on that interest will only impart clarity on whether that new venture is or isn’t for you. So with that in mind, don’t be afraid to take risks because regardless of the outcome, you’ll still manage to learn from the experience.